Ransomware a growing threat, extorts $5 million a year
Malware that disables computers and demands that hefty cash payments be paid to purported law-enforcement agencies before the machines are restored is extorting as much as $5 million from end-user victims, researchers said.
The estimate, contained in a report published on Thursday by researchers from antivirus provider Symantec, is being fueled by the mushrooming growth of so-called ransomware. Once infected, computers become unusable and often display logos of local law-enforcement agencies, along with warnings that the user has violated statutes involving child pornography or other serious offenses. The warnings then offer to unlock the computers if users pay a fine as high as $200 within 72 hours.
"A lot of individuals do pay up, either because they believe the messages or because they realize it is a scam but still want to restore access to their computer," Symantec's 16-page report explained. "Unfortunately, even if a person does pay up, the fraudsters often do not restore functionality. The only reliable way to restore functionality is to remove the malware."
The report identified at least 16 different ransomware versions spawned by competing malware gangs. Many are completely different families of malware, rather than multiple variants of the same family, and most have their own unique behavior. Many use freely available geographic location services to determine where each infected computer is and based on that information display law-enforcement logos and ransom demands that are local to that user. Demands frequently carry threats of arrest if victims don't pay promptly, usually by using electronic payment systems to purchase an unlock code.
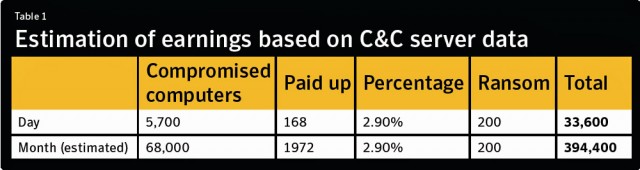
The Symantec researchers penetrated the command-and-control server of one ransomware scam. Over a period of about a month, between September to October, 68,000 unique IP addresses connected. During a single day during that time, there were 5,700 connections, and of those 168 entered what appeared to be valid unlock codes. Assuming 2.9 percent of the overall 68,000 infections paid the $200 fee, that would have net more than $394,000, although the scammers would have lost a percentage of that as they attempted to launder the money. The Symantec report doesn't explain precisely how the overall $5 million estimate was reached. Presumably, it is the result of factoring in the remaining ransomware operations.
The organization and proliferation of the scam has come a long way since the early days of ransomware several years ago. Back then, similar malware scams were limited mostly to Russia and Eastern Europe and often contained warnings in Russian that purported to be activation screens from Microsoft. Over time, the warnings began to make claims that users were in violation of local pornography laws and migrated west, to Germany, the UK, and Austria. More recently, the US and Canada have also been increasingly hit by the campaigns.
In some cases, the gangs operating the scams are also responsible for highly profitable operations that use malware to carry out bank fraud, indicating just how far ransomware has come.
"The individuals responsible for it are clearly professional criminals, and for them to have expanded into the distribution of ransomware is a sign of the profitability behind the scam," the researchers wrote.
